Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
4.9 (474) In stock
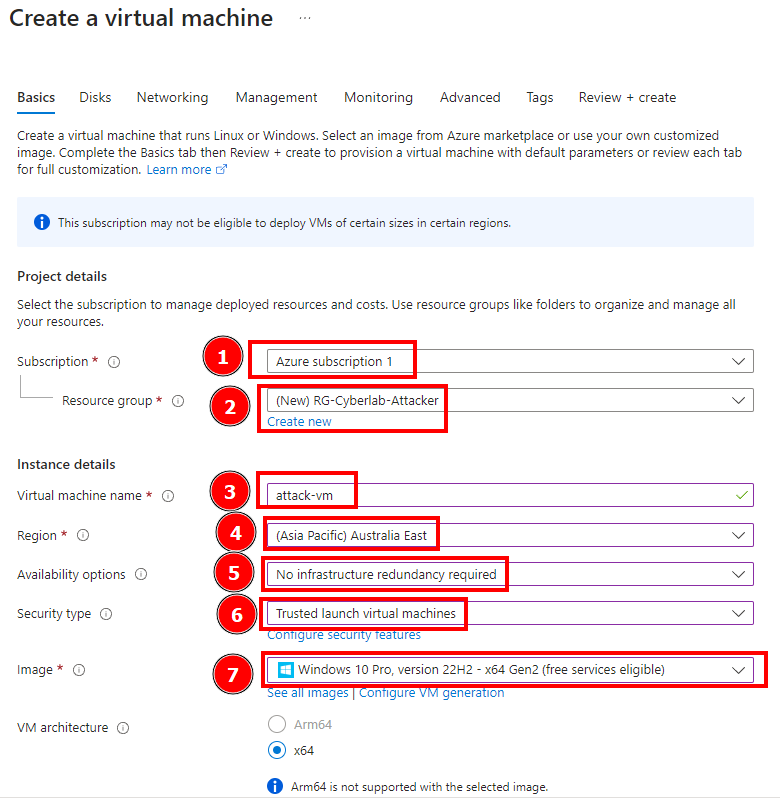
In this session we’re going to simulate an attack from another VM and then observe the attacker’s log. First we create an attacker VM. This VM’s name is attack-vm and also contain a different…

Guidance for preventing, detecting, and hunting for exploitation of the Log4j 2 vulnerability
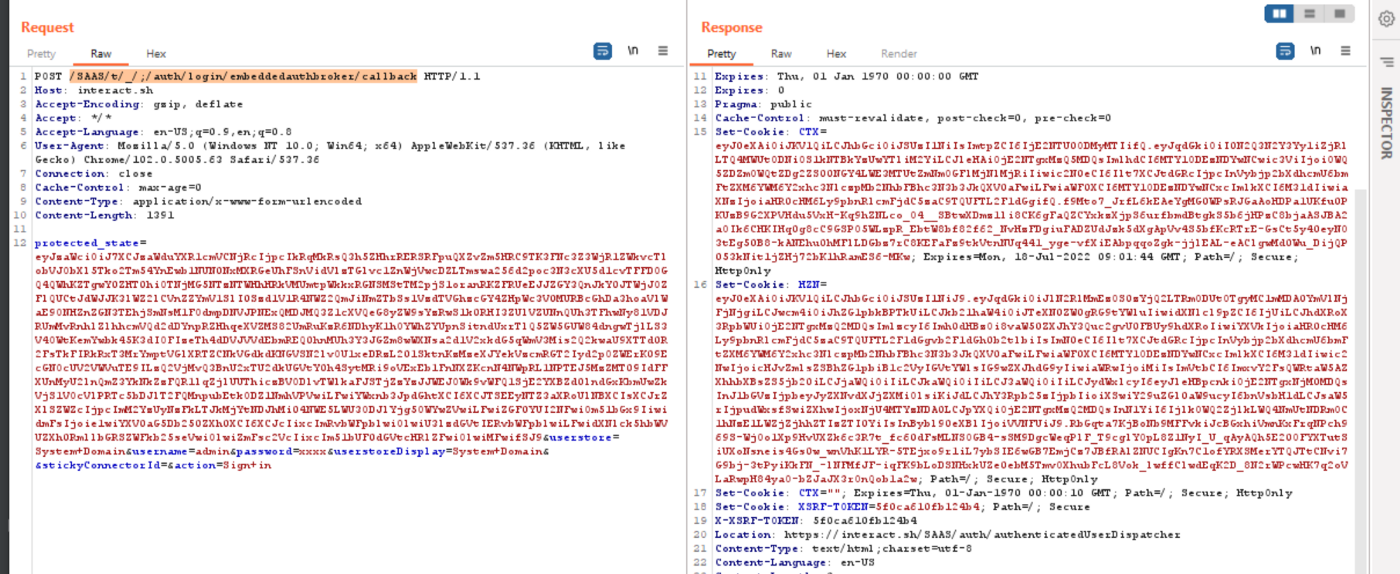
Public Exploit Available for Critical VMware Bug CVE-2022-31656 - Security Investigation

PDF) POIROT: Aligning Attack Behavior with Kernel Audit Records for Cyber Threat Hunting

Part 9: Microsoft Sentinel Incident Response., by Duyet Bui

Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui
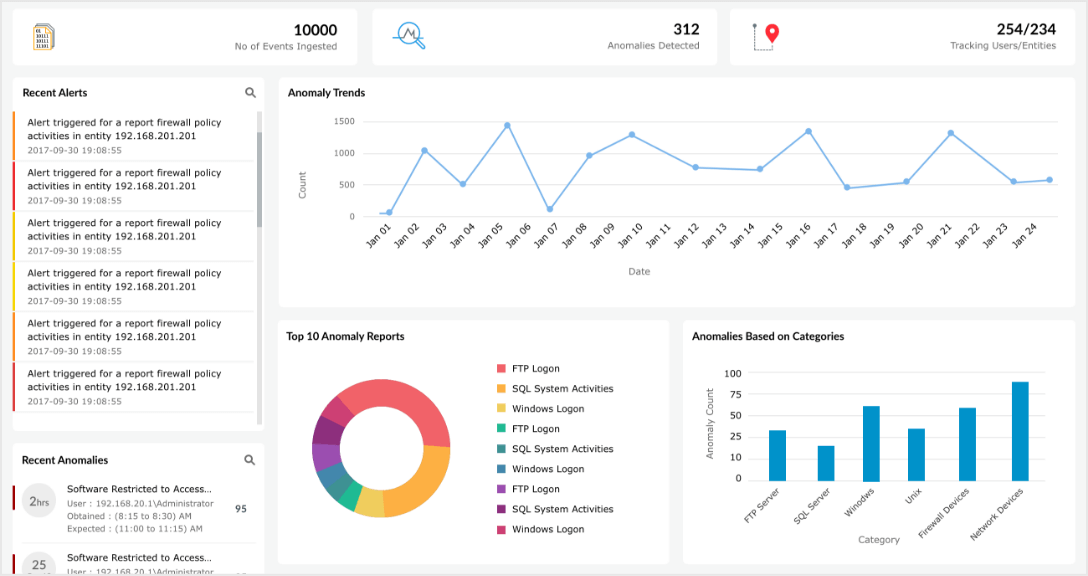
A comprehensive guide to DoS and DDoS attacks

Part 2: Attack Simulation from Another VM & Attacker's Log Inspection (Failed Authentication and Log Observation), by Duyet Bui

Scenario based attack simulation » 2
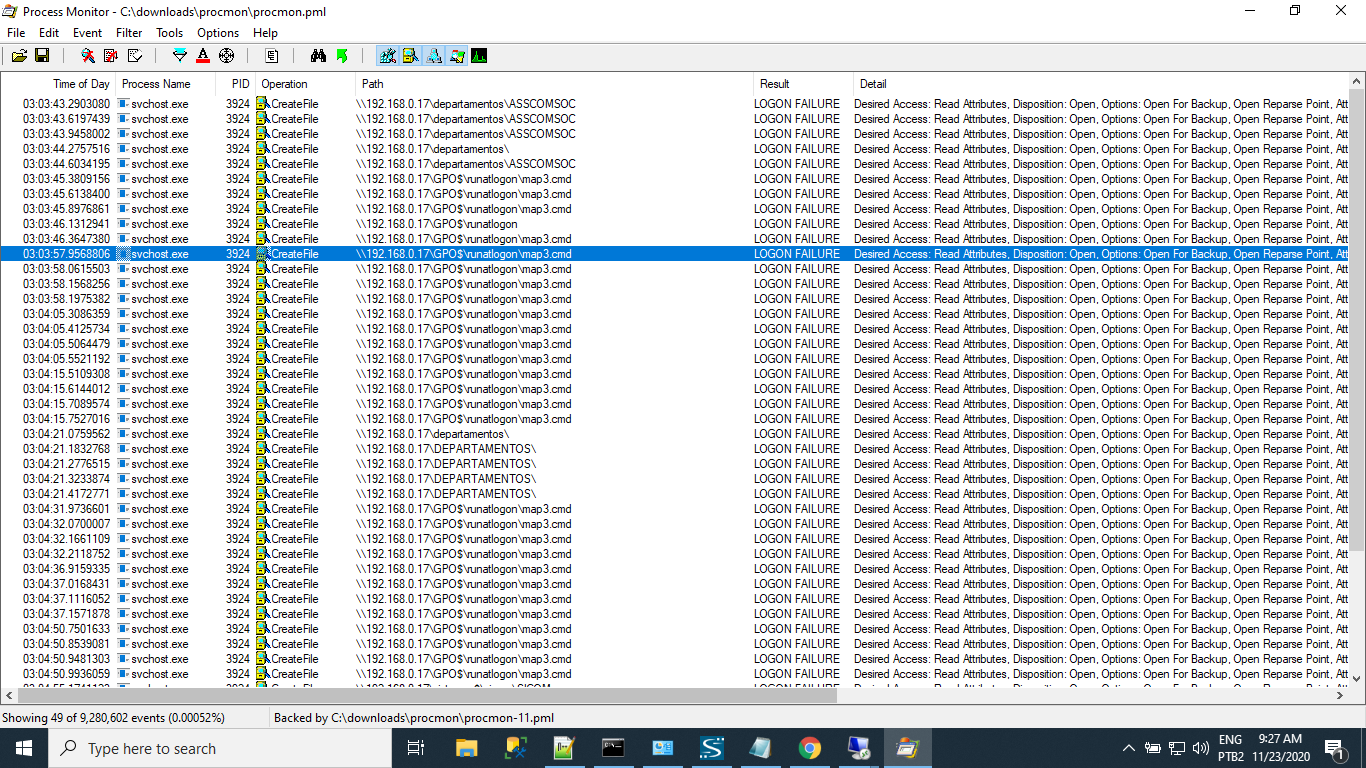
How to capture invalid login attempts? - Microsoft Q&A
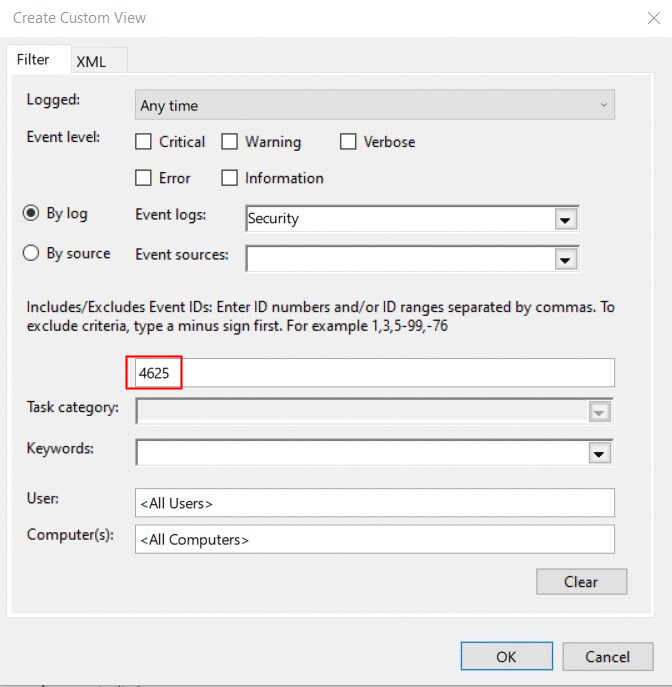
How to find failed login attempts in Active Directory
MANGOPOP Deep V Neck Short Sleeve … curated on LTK
Curling Canada Canada part of three-way tie at top of 2014 Ford Worlds
Find and remove duplicate references - EndNote desktop: self-paced
 Alpha Bra, Tank, and Dress
Alpha Bra, Tank, and Dress TWO PIECE SET Alexander Wang Ribbed Jersey Two Piece Set
TWO PIECE SET Alexander Wang Ribbed Jersey Two Piece Set Anita Sports Bra Active Extreme Control Max Support Sports Bras Non Wired
Anita Sports Bra Active Extreme Control Max Support Sports Bras Non Wired KDDYLITQ Women's Bra with Seamless Push Up Unpadded Lace Full Coverage Underwire Bras Plus Size Bra for Heavy Breast Blue 36D
KDDYLITQ Women's Bra with Seamless Push Up Unpadded Lace Full Coverage Underwire Bras Plus Size Bra for Heavy Breast Blue 36D Top Fitness alcinha Wonder Chumbo - Chlorella Praia, Biquínis & Fitness
Top Fitness alcinha Wonder Chumbo - Chlorella Praia, Biquínis & Fitness Men's Atlanta Braves Nike Navy 2023 NL East Division Champions
Men's Atlanta Braves Nike Navy 2023 NL East Division Champions